Two days of talks, workshops, hacking challenges and community.

Once a meetup of 30 students, LTDH is now Scotland’s flagship student-led cyber security conference - with hundreds of attendees, world-class talks, hands-on workshops and our legendary CTF.


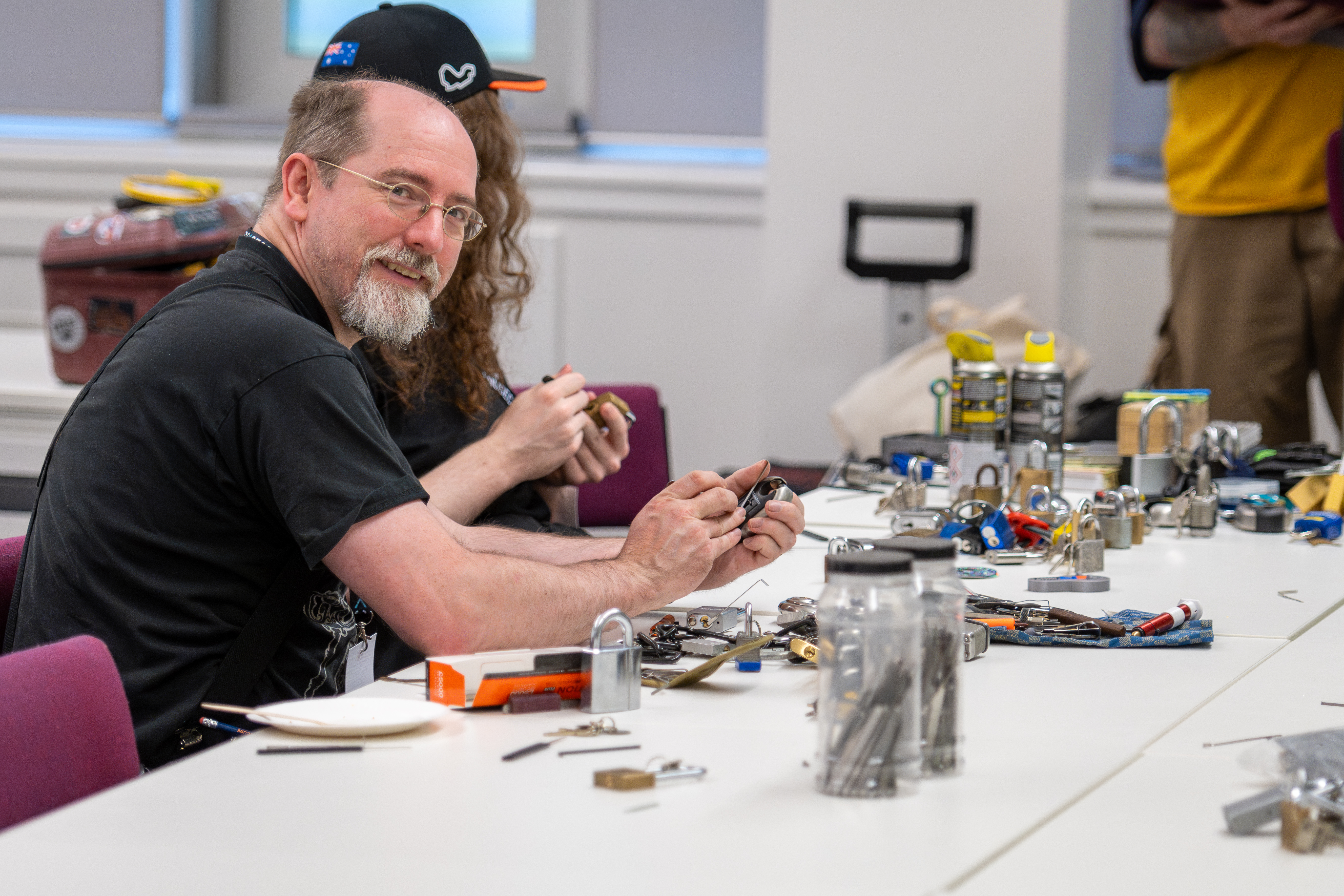
LTDH returns on May 16–17, 2026, hosted by ENUSEC. It's two days of learning, hacking, breaking things on purpose, fixing them again, and meeting people who love cyber as much as you do.
Talks that actually teach you something, workshops where you get hands-on, and our legendary Capture the Flag - a mix of caffeine, chaos, and clever thinking.
The real magic is the vibe - spontaneous debugging huddles, "wait I think I found something" moments, hallway chats, and meeting people who get why you love this stuff.
Help power Scotland’s next generation of cyber talent. Sponsoring LTDH means supporting a community built on curiosity, collaboration, and a little bit of hacker chaos.
From intro talks to deep-dive workshops, there’s something for every level - whether you're brand new or battle-hardened.
Our CTF is iconic - puzzles, challenges, mayhem, and the shared chaos of trying to beat the scoreboard before midnight.
Meet hackers, students, researchers, professionals, and friends-to-be. LTDH is known for its warm, welcoming atmosphere.
It’s a weekend packed with energy - laptops out, ideas flowing, last-minute fixes, high-fives, and plenty of caffeine. Whether you're cracking challenges, sharing stories, or discovering new paths in cybersecurity, you’ll leave inspired (and probably a bit sleep-deprived).
Full schedule coming soon
Two days of hacking, collaboration, inspiration and community.
The first day is all about ideas, energy, and community.
Attendees meet industry leaders, discover new tools, and connect with Scotland’s growing cyber community. It’s the perfect space for your brand to stand out, be seen, and make an impact.
After the day wraps up? It’s Afterparty time - where sponsors, speakers, students and industry professionals get to relax and enjoy the evening.
A full-day CTF where competitors race to solve challenges, climb the leaderboard, and push their skills to the limit.
It’s fast, fun, and unforgettable - and your name is right there alongside the action.
We end the event with awards and a celebration of the achievements of the day.

Day 1 features tracks packed with speakers from industry, academia and the hacker community. Expect practical talks, live demos, and sessions that leave you with something new to try the minute you get home.
Coming Soon
Opening Soon...
Speak at Le Tour Du Hack. We welcome talks from students, professionals, researchers, educators, and hackers of all backgrounds.
Talk categories include: technical research, hacker stories, blue team ops, cyber careers, demos, workshops, and more.